Smart Cloud or Smart Home: Stumbling Our Way Around Bad Actors in Consumer IoT
As the sun sets, I ask Alexa to turn on the deck lights so my wife and I can enjoy some time together after we tuck our children in. When I do that, the whole sequence looks like the following:
- Alexa takes my voice and digitizes it
- The digitized command is sent to the Amazon Cloud
- The audio is analyzed based on Amazon’s algorithms and guesses what I might have said
- Amazon then checks against my personal set of commands for my smart home stored in their cloud
- Once the “Turn Deck Lights On” is identified, Amazon then communicates to Wink that I have a command
- Wink authenticates that Amazon is able to make that request on my behalf
- Wink then sends the command to my local Wink hub over the internet
- My hub authenticates the command from Wink and, over the Z-Wave mesh network, tells the switch controller to turn on the smart plug associated with Deck Lights
With a noticeable delay, the lights come on and we continue with our evening plans of drinks, sunset and relaxation. But what I don’t think about everyday is how much of this “simple” command flow takes place outside my home, of how many potentially weak links there are in that chain. Given the number of “actors” involved in making this happen, any of these actors could be compromised, allowing our family’s data to be shared with others wholes goals do not align with turning on my deck lights. As we are learning from the headlines, there are an increasing number of bad actors seeking to do just that. Additionally, companies have left open loopholes in their own development efforts, accidentally, that expose users to new constellations of ramifications. The revelation that Twitter was storing our passwords in the open before securing is tantamount to banks leaving our cash in a paper bag on counter while the teller is on break before putting it in the vault. Twitter did not do it on purpose. They are, especially with the scrutiny that Facebook is under, typically one of the good guys in this balance between utility and privacy.
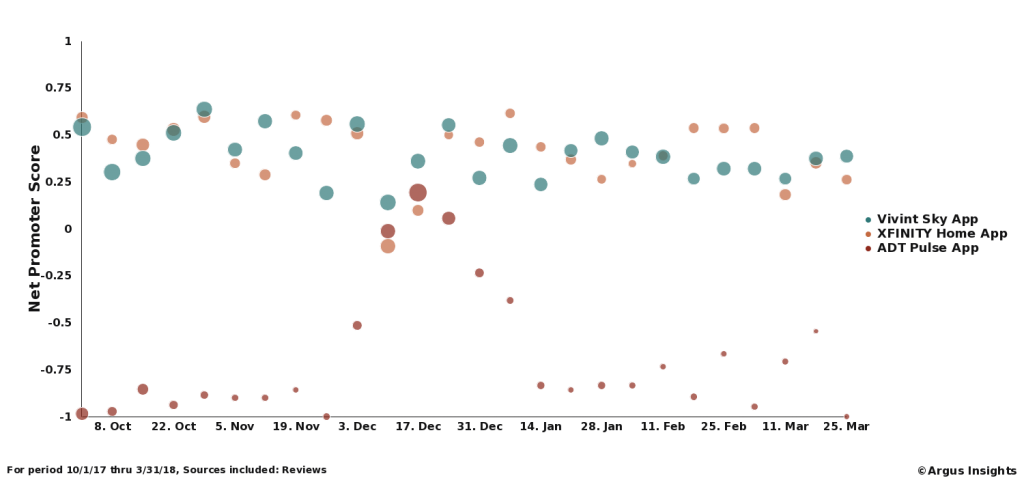
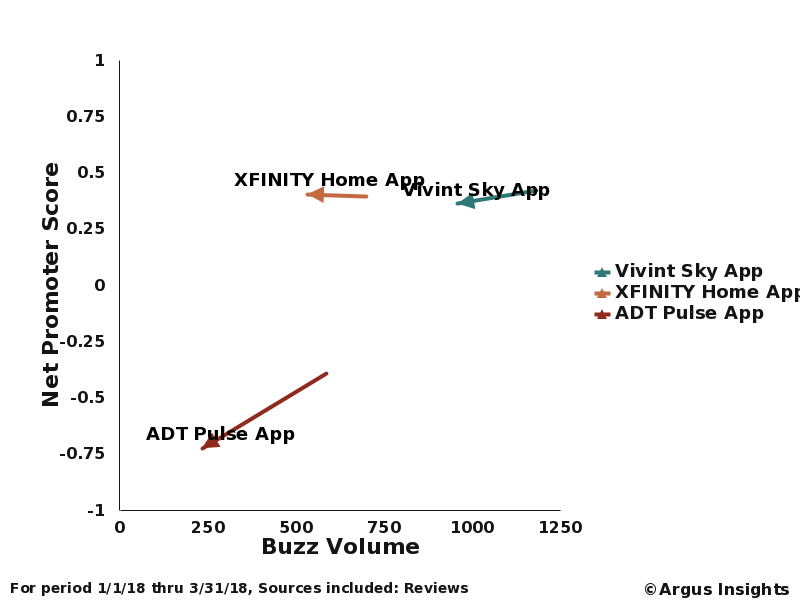
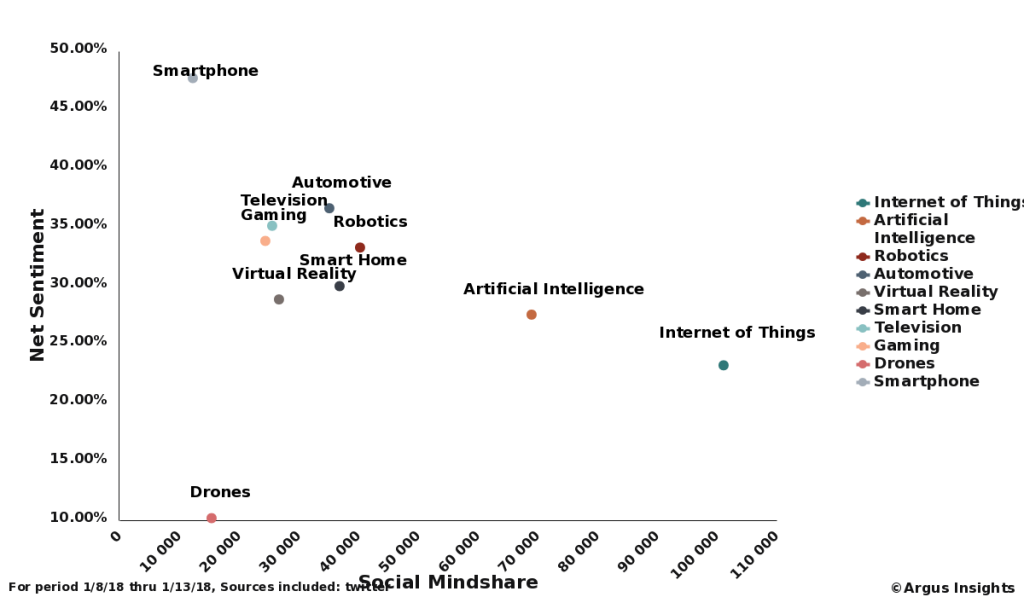
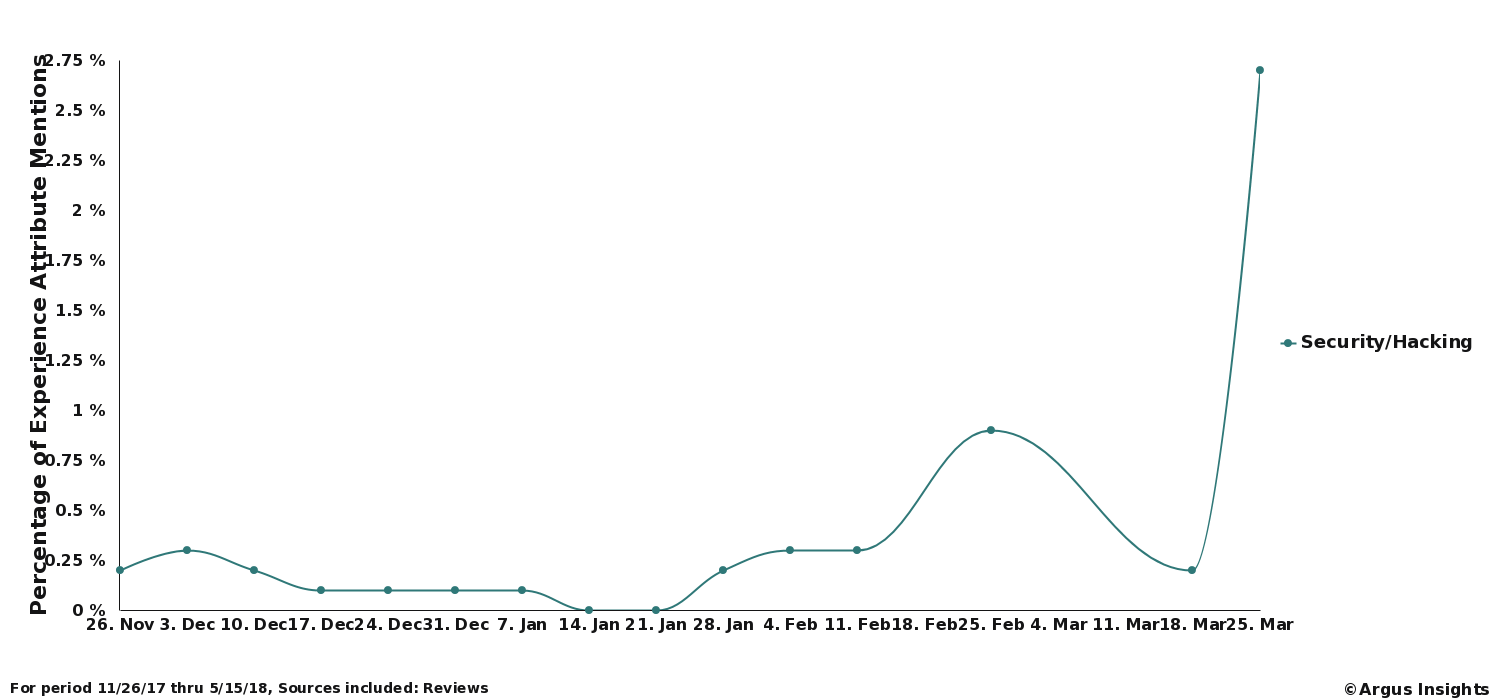
What are the chances that the devices and services we pull together to protect and control are home will be compromised in the near future? Very high, mainly because the extreme reliance on cloud services increases the attack surfaces available for hackers to take advantage of. We’ve actually seen a significant jump in consumer concerns on hacking in our tracking of the Smart Home market in the past few months.
There have been a few firms working to enable more localized control of the Smart Home. Hubitat is the most recent to launch a 100% local Smart Home solution. While they do not handle video integration, they can at least keep the deck lights scenario I mentioned above all in the family. Not only does the local control all but eliminate the delay in asking Alexa to turn on the deck lights, it all happens (except for the Alexa processing of my voice) locally. Especially if I have devices from multiple manufacturers, activating a scene like ‘date night’ dims the interior lights, turns on Barry White on the “Deck Group” and locks the front door, becomes instantaneous. This is a big step towards really securing the home from bad actors, both purposeful and accidental.
If you’d like to really understand what is happening in Smart Home, cutting through the promises to the meat of consumer reality, let us know. We have the data on over a million Smart Home consumers across the entire market. I’m sure we can help make you a Smart Home hero!